Why Your Digital Footprints Matter?
When it comes to protecting oneself on the internet, it is critical to discuss digital footprints and how they make you susceptible. Data security should be everyone’s top responsibility since it might put you or your company in danger. These are not something to take for granted.
Let’s explore what digital footprints are and how to hide them.
What Are Digital Footprints?
As the name implies, digital footprints are the imprints we leave behind when we surf the internet. It is the data trail we leave behind every time we visit a website. Even on social media, retail websites, food ordering websites, and every other website on the internet, our footprints are tracked and our information is obtained. Similarly, when we visit a dubious website, all of our phone’s data is stored, rendering us susceptible and putting us in danger. They gather all sensitive information and have the potential to leak or misuse it.
Unfortunately, many individuals are unaware of it and believe that every website is safe, which is false. Most websites these days are suspect, and we need protect ourselves from them because our device has all of the data. It can jeopardize the firm’s reputation, particularly for the company and its personnel.
Digital footprints are classified into four categories: public, private, IoT, and state activities. Most people are definitely unaware of it because these concepts are quite complex and require a particular degree of comprehension before delving into the issue. To summarize, everything we do on the internet leaves a data trail that might make it simpler for cyber-attackers to acquire access to our information.
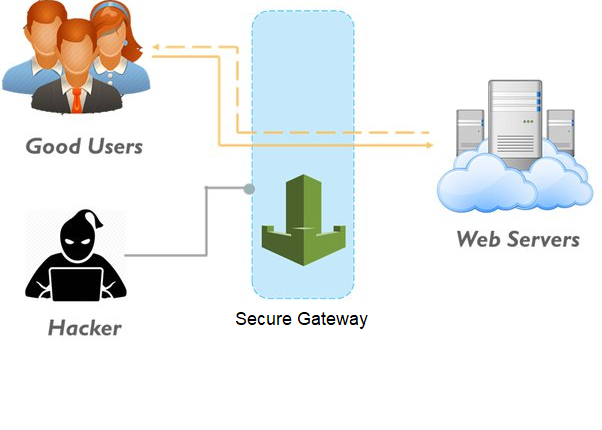
Secure Your Way Through Secure Gateway
Certain cybersecurity organizations operate around the clock to give protection to all of its clients. Since its start, Secure Gateway has assisted corporations in securing all government agencies, including the ministries of defense, interior, and trade. Furthermore, it offers all of the United Nations’ security and takes care of its digital traces.
You may be wondering how they accomplish this. So here’s the solution. They allow clients to host websites on their servers, allowing them to keep hackers at bay. They keep the servers to themselves because hackers infiltrate through them, therefore, it is really sensitive. Now, if a hacker enters the system, they must pass through the Secure Gateway’s stringent filtering, which allows them to detect all hackers.
Secure Gateway offers bare-metal and virtual server configurations, as well as a variety of operating systems, hypervisors, and database platforms. Virtual server configurations are available in single- or multi-tenant models, but bare-metal server configurations are only accessible in single-tenant mode.
Secure Gateway provides extensive integration and automation. All aspects of the service may be managed and integrated by administrators using a proprietary application programming interface (API), online site, and mobile applications. Administrators can use additional tools to transfer and scale bare-metal and virtualized server images as their needs change.
Secure Gateway is the future of cybersecurity organizations since it handles everything from A to Z for clients, so they don’t have to worry about it. They are already working on cutting-edge technologies, and you may entirely entrust them with your company’s server.

Comments are closed.